Enterprise businesses and government agencies around the world face the certainty of losing sensitive data from a lost laptop, removable media or other plug-and-play storage device. This drives the need for a complete data protection solution that secures data on all common platforms, deploys easily, scales to any size organization and meets strict compliance requirements related to privacy laws and regulations.
Check Point Endpoint Security solutions provide data protection for laptops, PCs, removable media and mobile devices. Our independently certified data security products ensure that our enterprise, government and law enforcement customers remain in compliance with regulatory standards. By leveraging a strong and efficient blend of full disk encryption, access control, removable media encryption and port management, Check Point Endpoint Security solutions deliver comprehensive data security.
The dramatic proliferation of laptops means your mobile workforce exposes large amounts of company data outside the secure perimeter of your office each day. Based on market-leading Pointsec® technologies, Check Point Endpoint Security Full Disk Encryption™ is proven in enterprises, businesses and government agencies around the world, providing the highest level of data security for laptops and PCs through a combination of pre-boot authentication and strong encryption algorithms.
| Comprehensive Protection for all Business Platforms |
 |
Windows |
 |
Mac OS X |
 |
Linux |
Centralized management ensures fast deployment, ease of administration and fully enforceable user compliance. Check Point Full Disk Encryption also operates completely transparent to the end-user providing a seamless introduction. Supporting all common smartcards / tokens and providing a rich feature set that includes Single Sign-On (SSO) and Windows Integrated Login (WIL), Check Point Full Disk Encryption can be easily configured to meet the needs of any organization.
How it Works
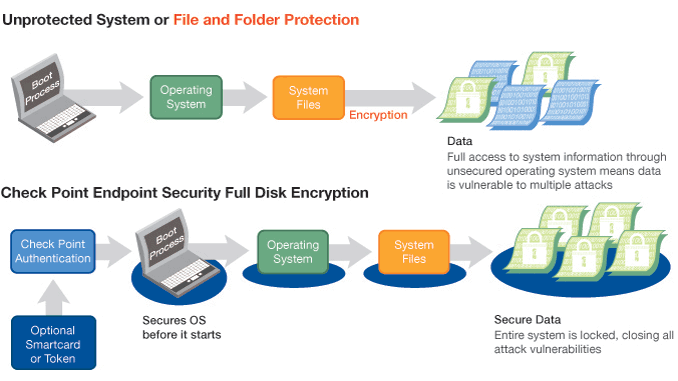
Clique na imagem acima para ver em tamanho real!
Benefits
- Prevents damaging data breaches resulting from lost or stolen laptops and PCs
- Deploys quickly on Windows, Mac OS X and Linux platforms to meet compliance objectives and conserve resources
- Scales to meet the needs of any size enterprise or government agency
- Windows and Mac OS X solutions are FIPS 140-2 compliant
- Simplifies central management for lower total cost of ownership
- Mandatory, enforceable data security policy
-
Check Point Media Encryption
Recent proliferation of USB ports and CD/DVD writers on laptops and PCs has dramatically increased the occurrence of data leak events within enterprises. USB flash drives, iPods, Bluetooth devices and removable media allow users to extract data in an instant —making all enterprise computers vulnerable. The ability to copy or move sensitive data onto these personal devices undetected places your organization at serious risk of untraceable dataleaks.
Check Point Media Encryption prevents unauthorized copying of sensitive data by combining port and device management, content filtering and centralized auditing with robust media encryption. Based on market-leading Pointsec technologies, Check Point Media Encryption plugs potential leak points and logs data movement to and from any plug and play devices, providing comprehensive control of security policies.

Government
Common Criteria and FIPS certifications
Check Point Endpoint Security solutions are Common Criteria and FIPS 140-2 certified among a longer list of certifications. Check Point was also the first security software vendor to achieve Evaluation Assurance Level 4 in Common Criteria quality certification (CC EAL4). And Pointsec Mobile was the first data encryption system to achieve FIPS 140-2 for Microsoft Windows Mobile 2003. Check Point will provide all certifications upon request.
Data Security Made Easy
Check Point Endpoint Security solutions launch prior to system start. Users only need to enter their passwords in a pre-boot window, and their systems will start up immediately. After that, the encryption process runs transparently, so users won’t even notice it. And it’s guaranteed that Check Point Endpoint Security solutions can be deployed in any size business or government agency.
Financial Services
Data Security Solutions That Can Be Trusted, Deployed and Used—Easily
Check Point Full Disk Encryption, Pointsec Mobile and Check Point Media Encryption can secure all the devices that an enterprise uses for financial services. Yet these solutions are quick and easy to deploy. In fact, they’re guaranteed. They’re also very easy for end users to work with—the only change that they will experience is a different log-in screen.
Mobility is Necessary, Compliance is Mandatory
Customers demand access to their funds and personal financial data. But laws in the United States (U.S.), the European Union, Japan and other regions demand the protection of customer privacy. Check Point helps fulfill both demands, while reducing legal exposure. And Check Point Full Disk Encryption, Pointsec Mobile and Check Point Media Encryption have been validated with security certifications for the U.S., Europe and other regions (FIPS and Common Criteria), plus BITS for the financial industry.
In fact, having a suite of Check Point Endpoint Security products shows everyone that an enterprise is serious about data security—customers, shareholders and even courts of law.
Protect Data, Reputations, Jobs
When equipment is lost or stolen, private financial data can be compromised. Corporate reputation and brand image can be seriously damaged. A company may be exposed to civil and criminal liability. And, if the data wasn’t protected, IT and security jobs may be on the line.
Don’t wait any longer. Choose the data security software thousands of financial institutions use worldwide. Choose Check Point Endpoint Security solutions.
Healthcare
Check Point Full Disk Encryption, Check Point Media Encryption and Pointsec Mobile—Ideal Protection for Today's Mobile Medicine
Ironically, these tough privacy regulations come just as doctors, nurses and hospitals need more and faster wireless information sharing to improve care and cut costs.
That's why data encryption delivered by Check Point Full Disk Encryption, Check Point Media Encryption and Pointsec Mobile from Check Point are ideal. All three solutions provide strong encryption that works in the background and is completely transparent to the user. The user need only enter a password in the pre-boot window, and the system starts right up.
The encryption performed by Check Point Full Disk Encryption and Pointsec Mobile meets both FIPS and Common Criteria standards. And it’s guaranteed that Check Point Endpoint Security solutions can be deployed in any size business or government agency.
Technology
Powerful Encryption Made Easy
The full disk encryption solution provided by Check Point begins immediately at startup. Users need only enter their passwords in a pre-boot window and their systems will start up. After that, the encryption process runs transparently, so users won’t even notice it. Check Point Full Disk Encryption can be customized for specific security needs so that it can work with all common smart cards, tokens, Single Sign-On, and Windows Integrated Login—as well as other data security solutions such as Check Point Media Encryption for flash drives and removable media and Pointsec Mobile for PDAs and smart phones—providing a number of easy-to-use options. And it’s guaranteed that Check Point Full Disk Encryption can be deployed in any size business or government agency.
Common Criteria and FIPS certified
Check Point Full Disk Encryption is both Common Criteria EAL 4 and FIPS 140-2 certified among other notable certifications. In fact, no one offers more—or higher levels of—certifications, for as many platforms as Check Point.
OMB Directive
Check Point Data Security Solutions are the Most Widely Deployed—for Good Reason
Because Check Point Full Disk Encryption, Pointsec Mobile and Check Point Media Encryption are highly scalable, quick to deploy and easy to operate with centralized management, they have become the most widely deployed full-disk encryption products throughout the U.S. government. Well in excess of 100,000 PCs and laptops are protected at more than 100 U.S. government agencies, departments and facilities. Those organizations have already done the research and comparisons—take advantage of their analysis and go with the solution that fellow government officials have already successfully deployed.
Meet Directive Requirements and More
The data encryption delivered by Check Point Full Disk Encryption and other data security solutions from Check Point fulfill OMB directive requirements and go further to address other government security requirements that may be required (such as HSPD 12 and teleworking support).
- Encrypt all data on mobile computers: use Check Point Full Disk Encryption for notebooks and laptops (either Windows- or Linux-based), use Check Point Media Encryption for portable storage media such as USB drives and writeable CD/DVDs, and use Pointsec Mobile for mobile platforms such as PDAs and smart phones

